In the previous post; during November 2023 failed login attempts predominantly from China, went undetected. Attacks from IP addresses* originating in Iran were always detected and demonstrated a very different strategy. This analysis highlighted poor record keeping for changes to the firewall system.
Takeaways
- Geographic Region blocking is effective
- Accidentally turning it off demos this
- Not being able to find the date of the accident, highlighted inadequate documentation.
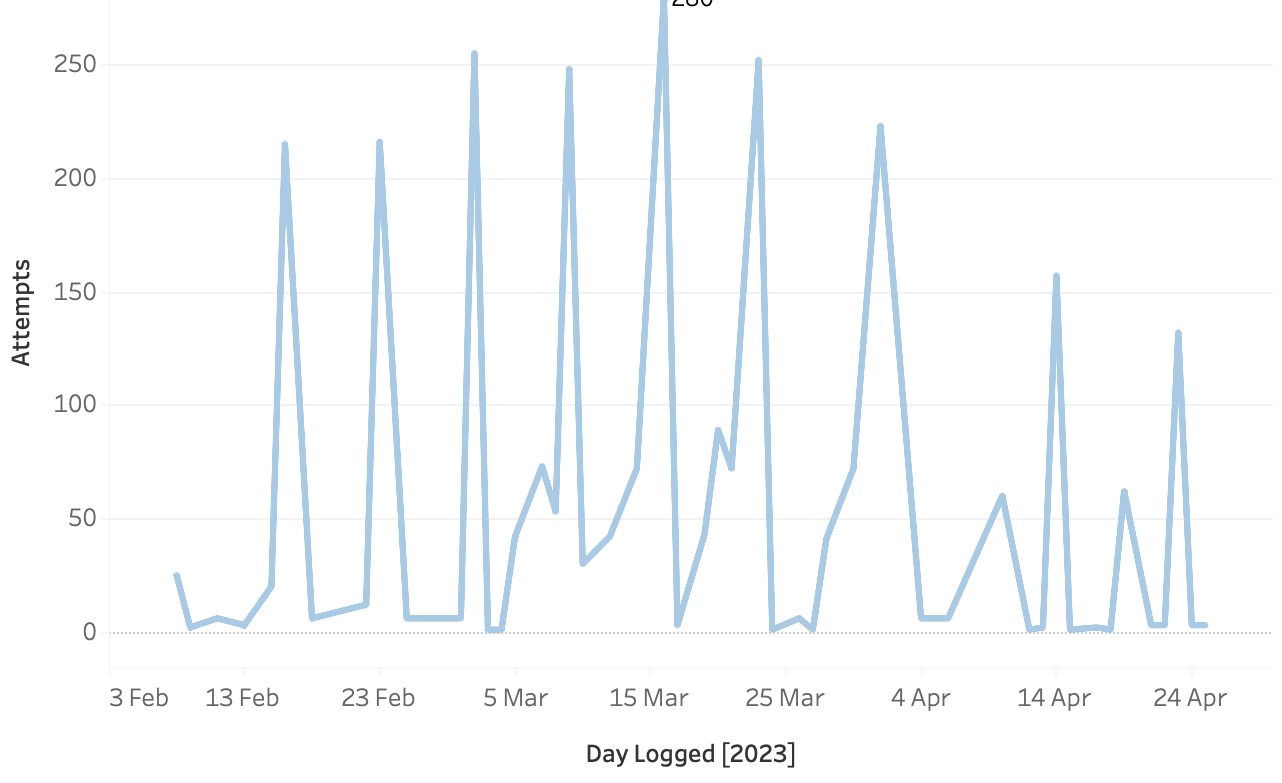
Returning to the original tableau graphic from the “Shields Up” post, showing failed login attempts by country per day on the server.
Blue spikes starting in mid February show failed logins from Iran. The rapid drop off is due to software implementing a ban targeting individual computers. If it were not for this software there would be a plateau of IPs probing. After a specified number of attempts an IP address is blocked for a number of hours. The computer is then unblocked in case it was user that forgot their password or an infected computer is cleaned. If failed logins continue, another program bans the IP for a longer time. **
* Notes
* for the purposes of banning hostile logins it is assumed that an IP address is a computer, in reality an IP address could be a router, the “computer” could be anything on the network behind the router including doorbells, web cams etc…
** The banning methodology can be problematic in an office with multiple staff members on a different network. If one user has incorrect details, the router can be blocked and everyone on the external network is then blocked.
What was seen was the firewall banning chunks of IP addresses from Iran. Roughly 150 of these were from a very similar set of numbers, so it was very obvious. Restricting the graph to a more limited time span and focussing on Iranian IP’s.
1st Tactic, Scouts and Squads.
There is a fuzziness to the bot net, the group seems split into sets of less than 25 computers. Some basic maths should highlight that something’s not quite right with the figures. 5 attacks from 150+ computers should be a peak of 750 attempts not a peak of 280. The numbers are misleading, splitting the computers into batches below:
Group H for example (brown) is present every large peak, but then it splits off on 10th April, K and I could have been combined, but Group I (pink) disappears entirely from 23rd April. Group D (red) always appears before the main spikes. What appears to be happening is that in Group A there seem to be “scouts”.
From the botnet’s point of view this makes sense, “scouts” which may not be from Iran, probe and add an entry to a database defining when a server is most likely in an unbanned state, “squads” are then dispatched. They appear to report back when they’ve been banned and the length of the ban time is then calculated by the botnet.
The geographic banning was implemented at the end of May, the scouts still hung around. Sometime in July the geographic banning was turned off by mistake. The scouting computers were still probing at a low level all during the geographic ban, on 20th and 22nd bans of Group A computers happened. On 17th July, when Group A found it could get through, it informed other groups. In this instance, a user error taught us more information about the Iranian botnet’s behaviour. It does seem quite likely that Iran is keeping to a 300 failed logins a day across its squads of computer.
In an ideal world, banning scouts would give the minimal set of firewall rules to ban the whole botnet. However it is impossible to work out which individual computer is doing the scouting, it is likely that some scouts are external to Iran. Every piece of information is useful to the botnet. If an Iranian scout never gets through but a non-Iranian is unblocked every 7 days, the botnet knows that some form of geographic blocking is in situ.
2nd Tactic, Hitting Hard.
Over the 320 day period and 30483 failed logins
- Iran tested 4469 username/ password combinations
- China tested 5834
- Iran had 2.2% of the total computers
- China had 24.3%
The Iran based botnet has 195 computers available. The China based botnet has over 2000 computers. In terms of efficiency, Iran managed many more attempts per computer than China (~23 Iranian attempts per computer vs 2.7 from China).
SQL Code.
SELECT country,
COUNT(logged) attempts,
ROUND(COUNT(logged)/30483*100,2) `% of attempts`,
COUNT(DISTINCT ip) `no of IPs`,
ROUND((COUNT(DISTINCT ip)/8858)*100,2) `% of IPs`,
ROUND(COUNT(logged)/COUNT(DISTINCT ip),2) `attempts_per_ip`
FROM all_country
GROUP BY country
ORDER BY attempts DESC
LIMIT 10 ;
| Country | No. of attempts | % of attempts | No. of IPs | % of IPs | attempts / IP |
|---|---|---|---|---|---|
| China | 5834 | 19.1 | 2153 | 24.3 | 2.7 |
| Iran, Islamic Republic of | 4469 | 14.7 | 195 | 2.2 | 22.9 |
| United States | 3252 | 10.7 | 956 | 10.8 | 3.4 |
| India | 2435 | 8.0 | 1015 | 11.5 | 2.4 |
| Lithuania | 2010 | 6.6 | 61 | 0.7 | 33.0 |
| Korea, Republic of | 1660 | 5.5 | 552 | 6.2 | 3.0 |
| Brazil | 1227 | 4.0 | 444 | 5.0 | 2.8 |
| Russian Federation | 1013 | 3.3 | 397 | 4.5 | 2.6 |
| Bulgaria | 935 | 3.1 | 114 | 1.3 | 8.2 |
| Taiwan | 705 | 2.3 | 354 | 4.0 | 2.0 |
The Iranian computers login as many times as they possibly can, get banned, come back and do it all over again. The scouts hang around even 2 months after a ban checking for changes in configuration. In terms of limited resources for the Iranians this is very effective, however it’s very visible and resulted in the geographic IP block which has been very successful.
China sending one attempt per computer is very stealthy, it was only visible because instead of the normal 100 computers a day, 10x the computers were sent (from many countries) over a 2 1/2 day period. The Chinese bot net is probably still active but at the reduced 100 computers a day is very difficult to counter. A mitigation would be extending the logging history of failed attempts, however with multiple stages compromising of
- Rate limiting to the email program
- Short term bans
- Long Term bans
- Geographic banning
the email server is working well within specification, but what happened next was the failure of the short and long term banning software.